3ds Max Software Security
CONTEXT
Every year, the Autodesk’s Infrastructure Security Team conducts penetration tests on all Autodesk products. That team’s mission is to discover security vulnerabilities in Autodesk products and services before the hackers do.
PROBLEM
The security assessment highlighted a number of high-risk areas in 3ds Max, mainly regarding a lack of restrictions and controls on external scripts and plugins. One of the main security vulnerabilities was that 3ds Max would load and execute scripts and plugins, even those embedded in .max files, without user content or awareness. These scripts and plugins, could then be used to execute arbitrary and malicious commands on the host machine.
MANDATE
Having just joined the security team, my mandate was to understand the user’s sentiment towards software security to be able to design a security layer that would help strengthen 3ds Max security, without being too restrictive. I collaborated mainly with the product owner and the tech lead to come up with a solution that would be feasible, secure, adopted by users and compliant with Autodesk’s security policy.
DESIGN PROCESS

User Research

User Interface

Design Thinking

UX for VR

Usability Testing

User Flows & Prototyping

Visual Communication

Quantitative Research
QUALITATIVE RESEARCH
Considering that none of the members of our cross-functional team was particularly familiar with software security or knew how to solve this specific security vulnerability, we started by doing semi-structured interviews with some of our most vocal beta users. We interviewed 9 of them, which gave us good foundational knowledge. However, all of them had a similar background and expertise; almost all of them were not artists; they were technical people like Technical Directors or Pipeline Directors (which meant that they were very familiar with scripts and plugins). They were all power users of 3ds Max and most of them worked in somewhat large companies.
QUANTITATIVE RESEARCH
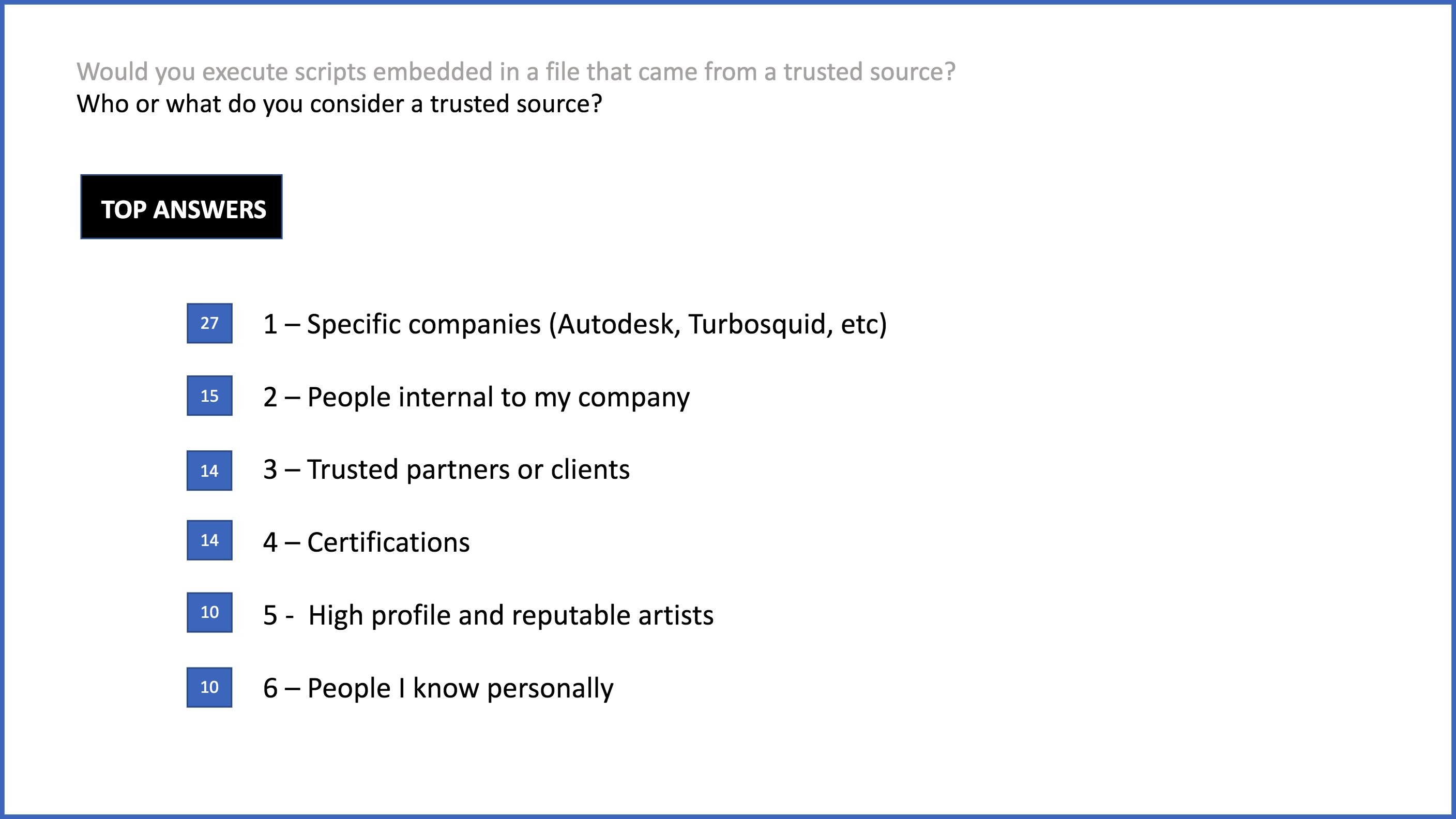
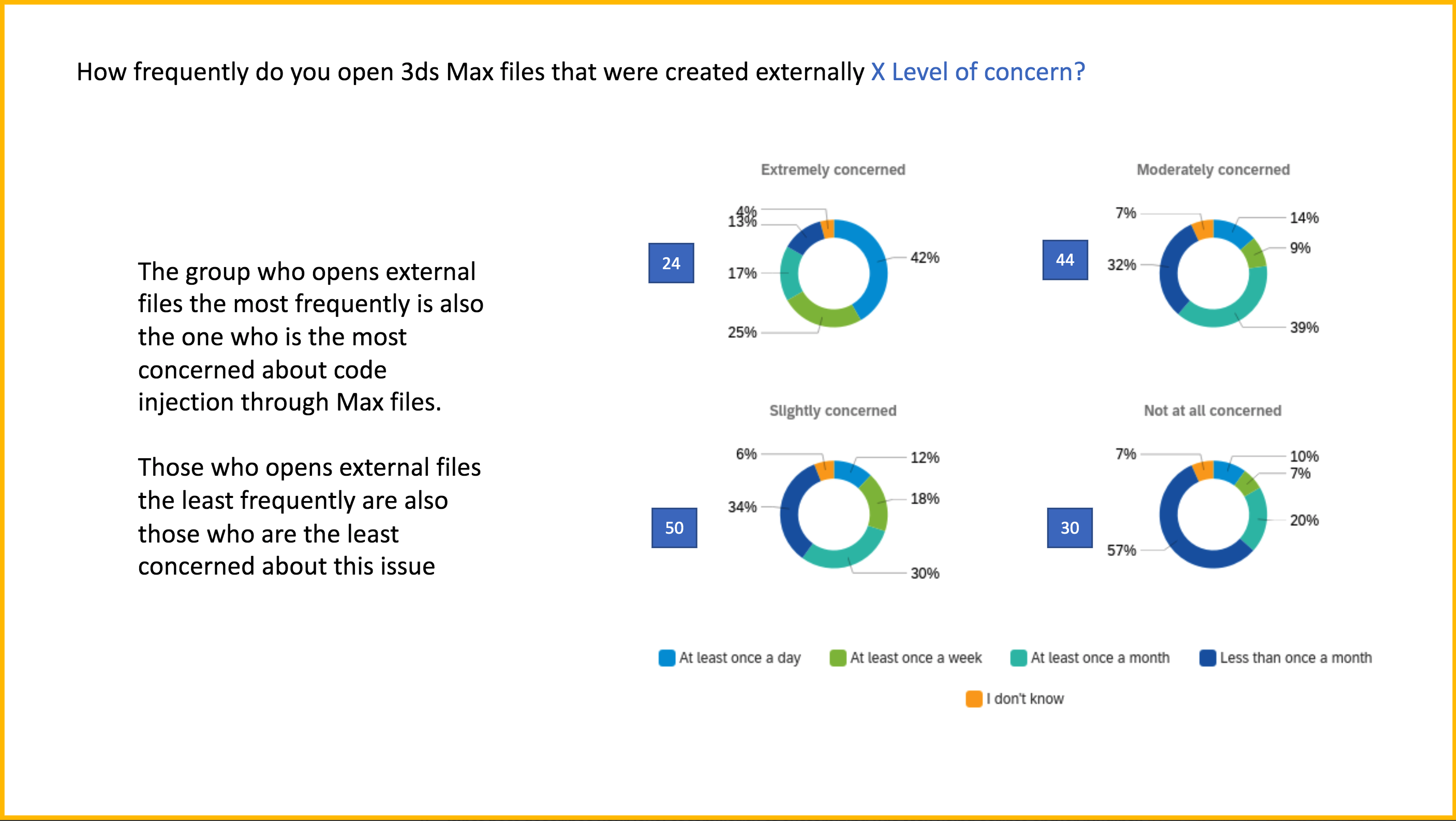
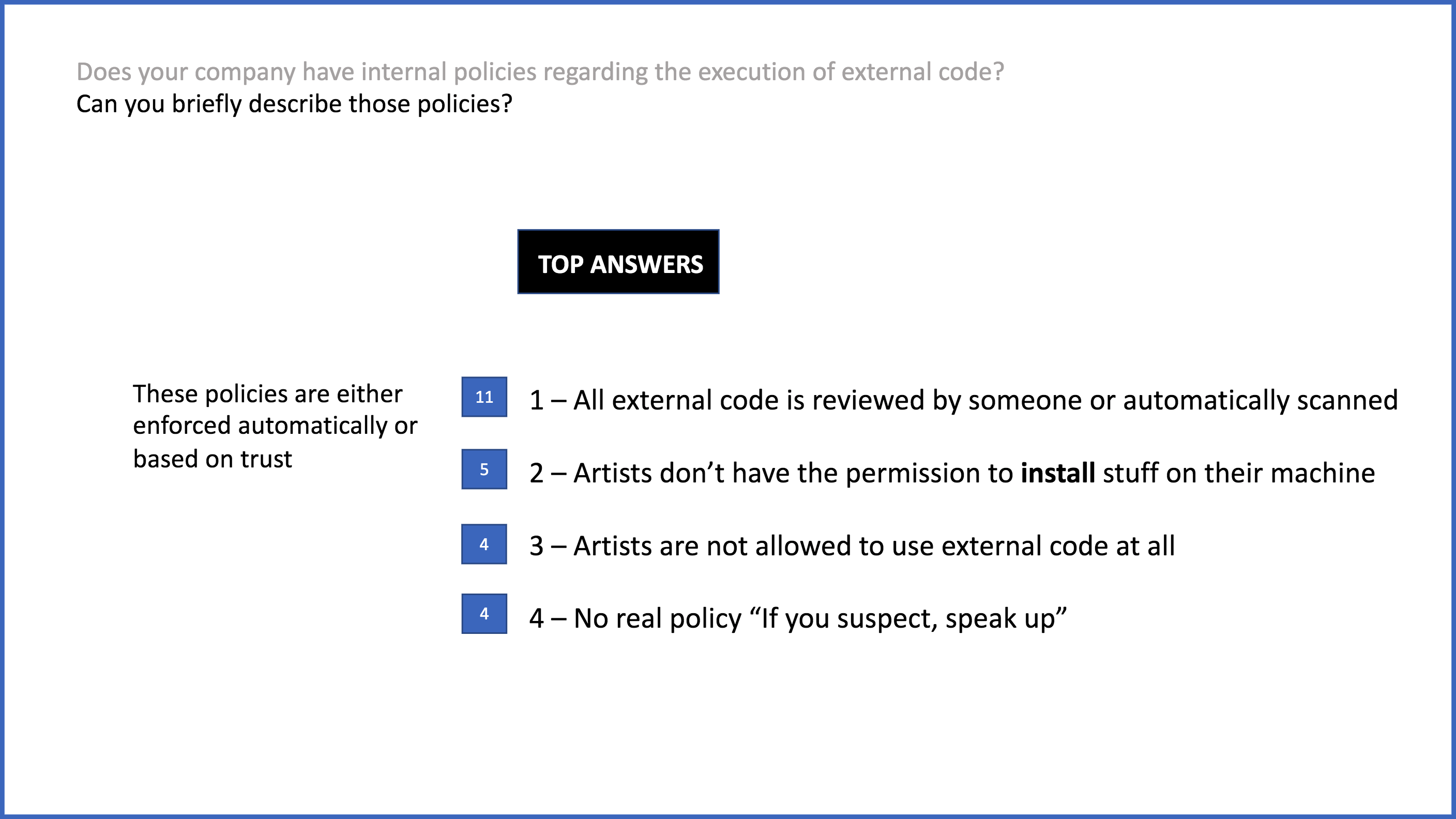
While we got very insightful feedback from our qualitative interviews, we needed to make sure that they were representative of our wider user base. For that reason, I suggested to do quantitative research. We needed to deeply understand our user’s sentiment towards software security before rolling out a solution that would eventually become the default for all our 3ds Max users. Autodesk wanted us to be more secure, but did our users even care? Were they concerned by software security? How frequently were they opening files from third-party? In order to answer those decisive questions, I created a survey using Qualtrics and sent it to all our roughly 600 beta users.
I HAD MANY QUESTIONS


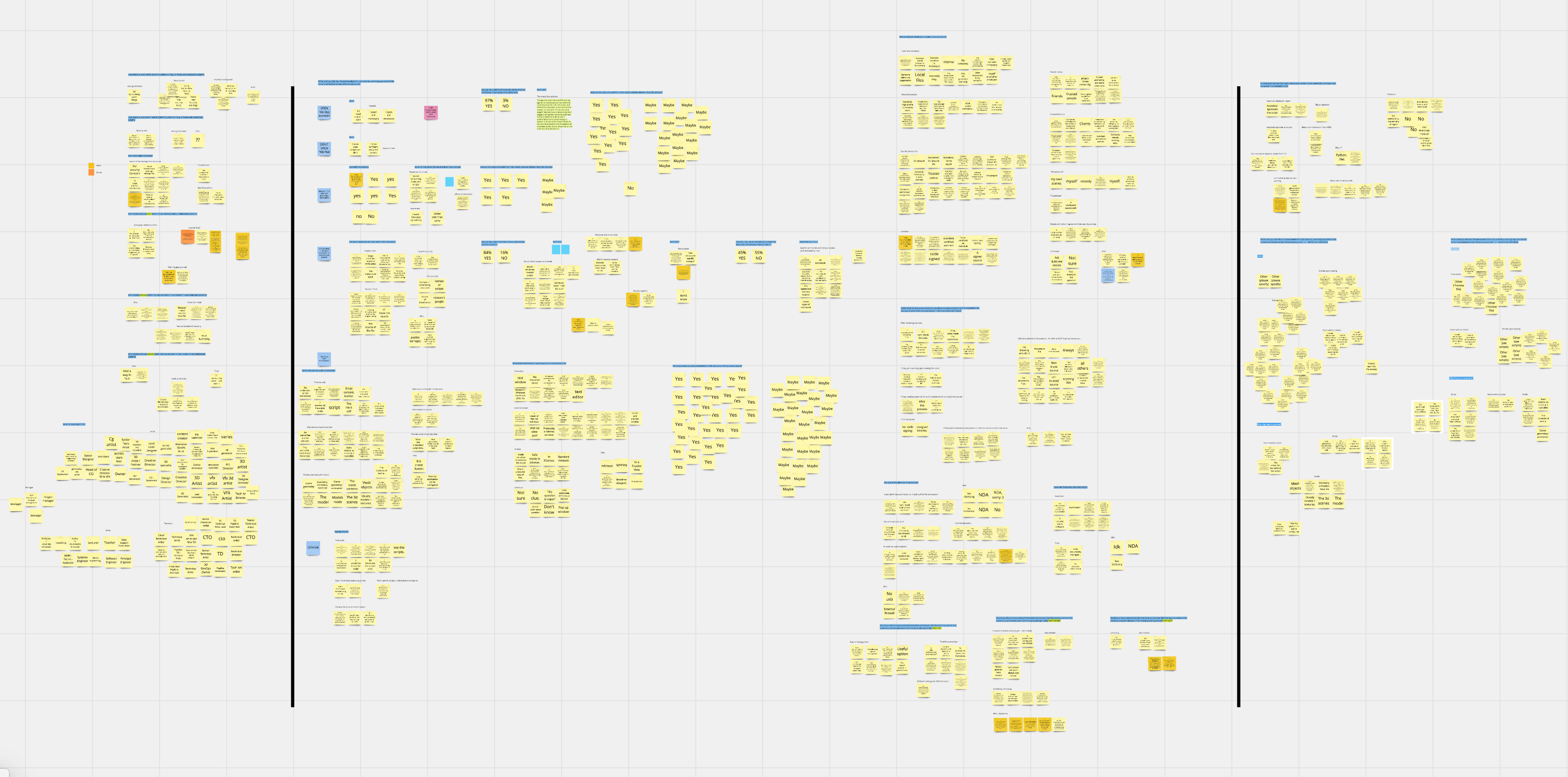
USED AFFINITY DIAGRAMMING TO MAKE SENSE OF THE DATA
While Qualtrics is very good at generating graphs and data visualizations, many of my questions included an open-ended comment section, which required a little extra work to analyze. To fully make sense of the data, I did affinity clustering using Mural.
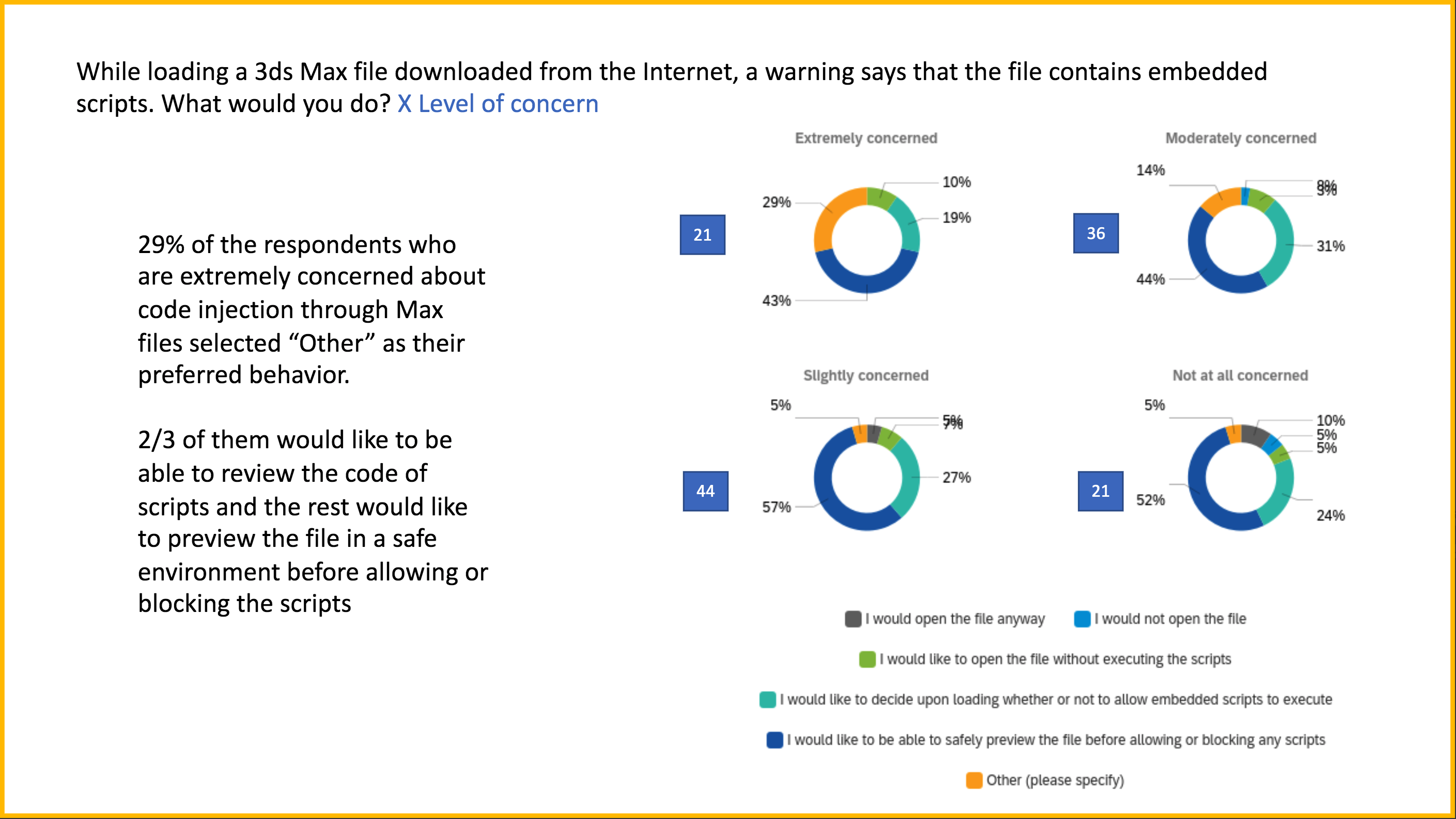
KEY INSIGHTS
The result of the survey highlighted many concerns, desired solutions and usage patterns, many of which were completely different from those heard during our semi-structured interviews. While this was unsurprising, our biggest takeaway was the following.

SHARED FINDINGS WITH STAKEHOLDERS
With all this precious data, both qualitative and quantitative, it was time to share our findings with the wider agile team to ensure that all members and key stakeholders were on the same page.
SOLUTION
Based on the learnings from our research, we identified 5 mitigation layers that would help strengthen 3ds Max software security.
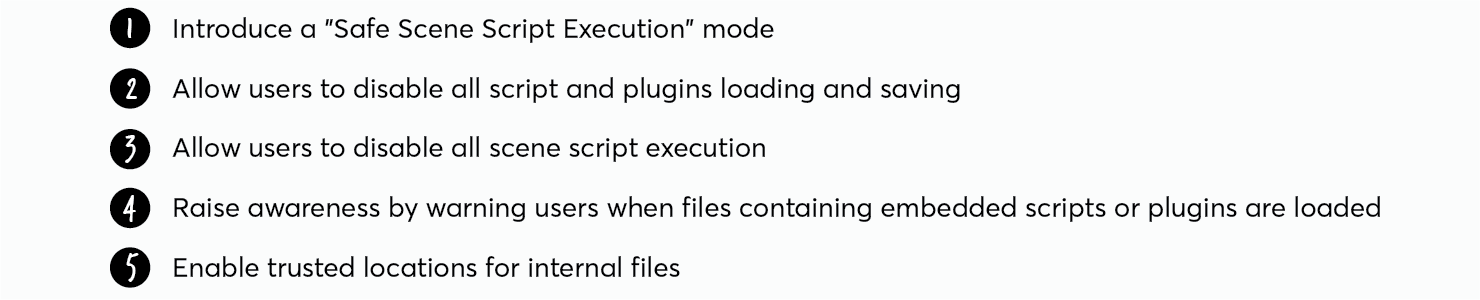
SAFE SCENE SCRIPT EXECUTION : OUR CORE MITIGATION LAYER
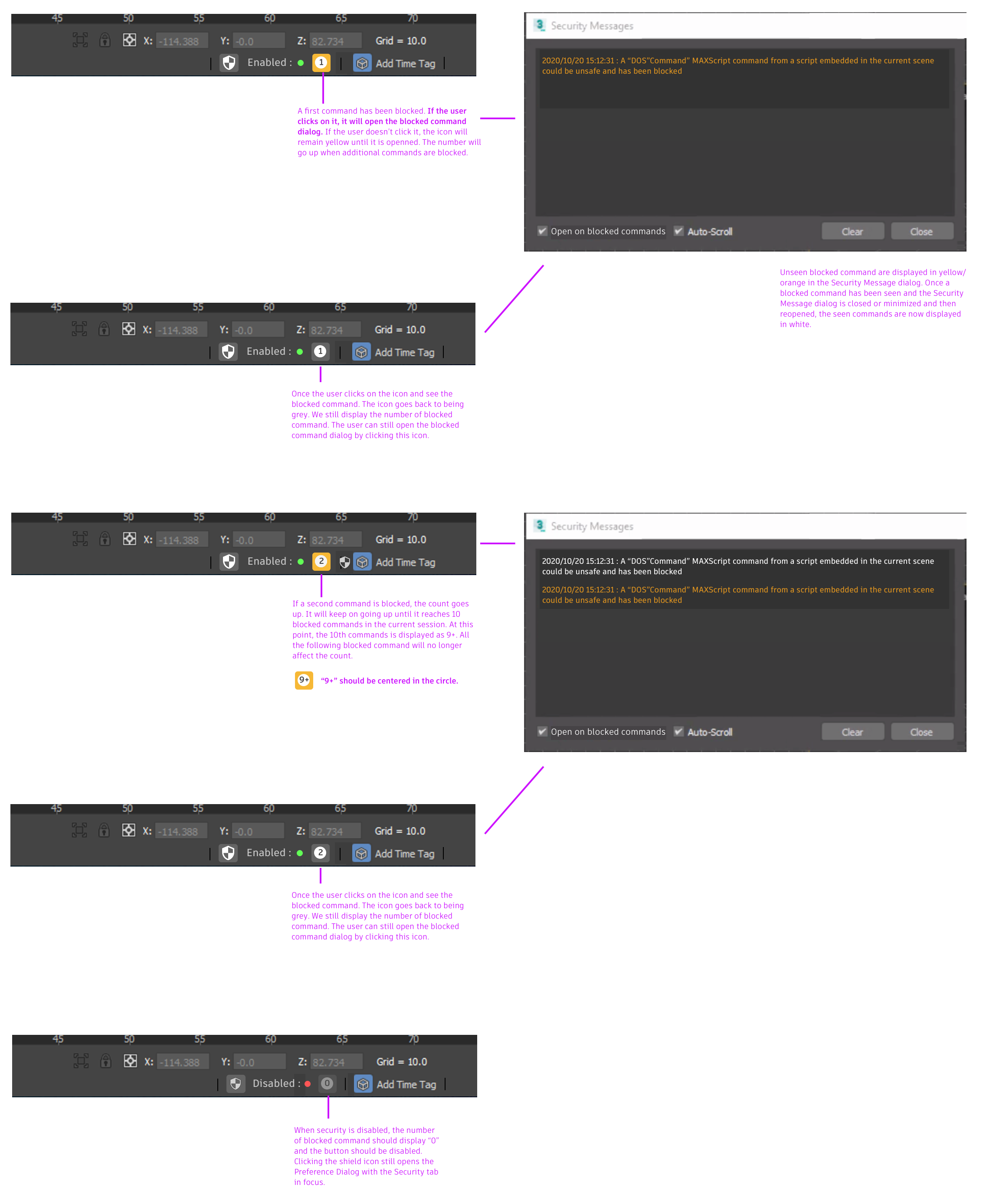
Knowing that most of the 3ds Max users are artists, and that according to our findings, most artists do not really care about software security and only want to be warned when REALLY malicious commands are detected, we decided to introduce “Safe Scene Scene Execution”. This mode, enabled by default, allows 3ds Max to detect scripts embedded in 3ds Max scene files and block them from executing potentially malicious commands at runtime (which prevents false positive/negative). In order to reduce the number of pop-ups and intrusive messages, I designed a minimalist Security Status bar and added it directly in the toolbar. While being very compact, this widget allows users to understand at a glance whether or not any commands have been blocked, find more information about them, adjust security settings, etc
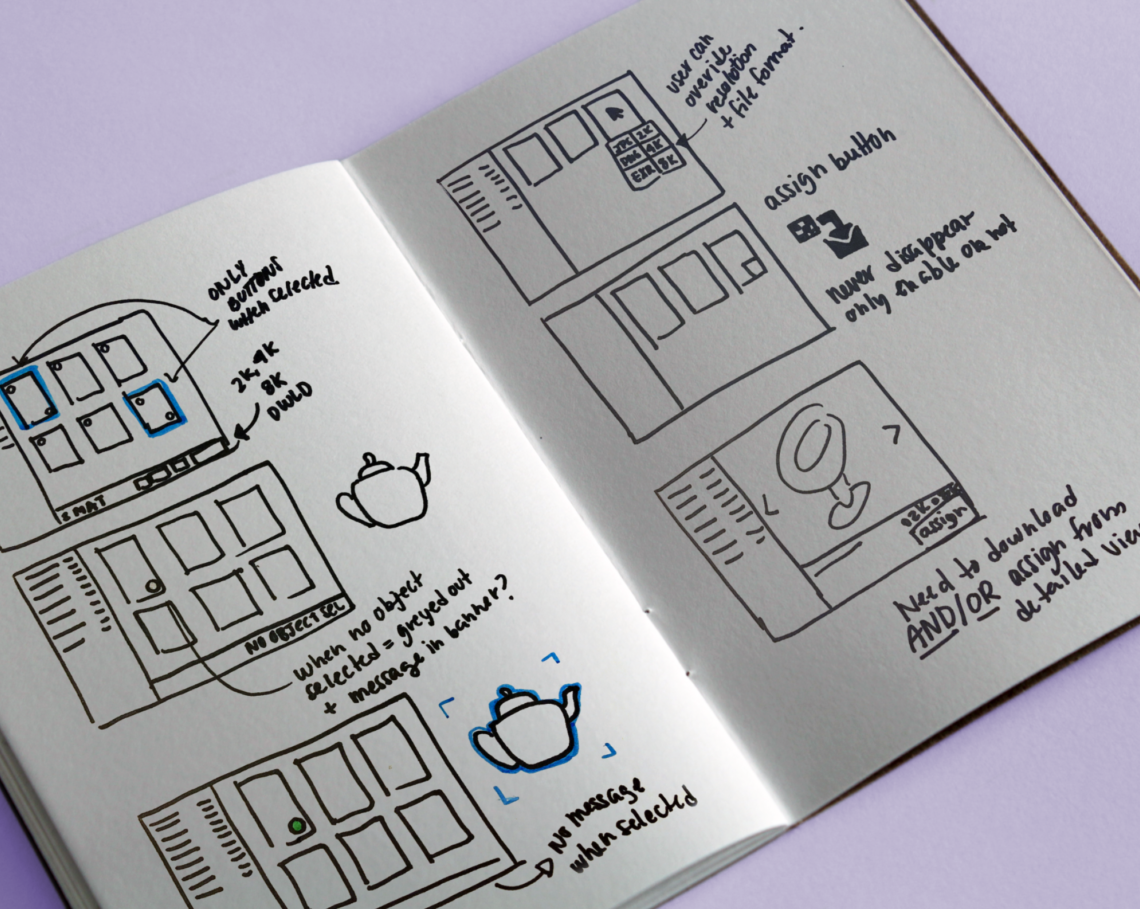
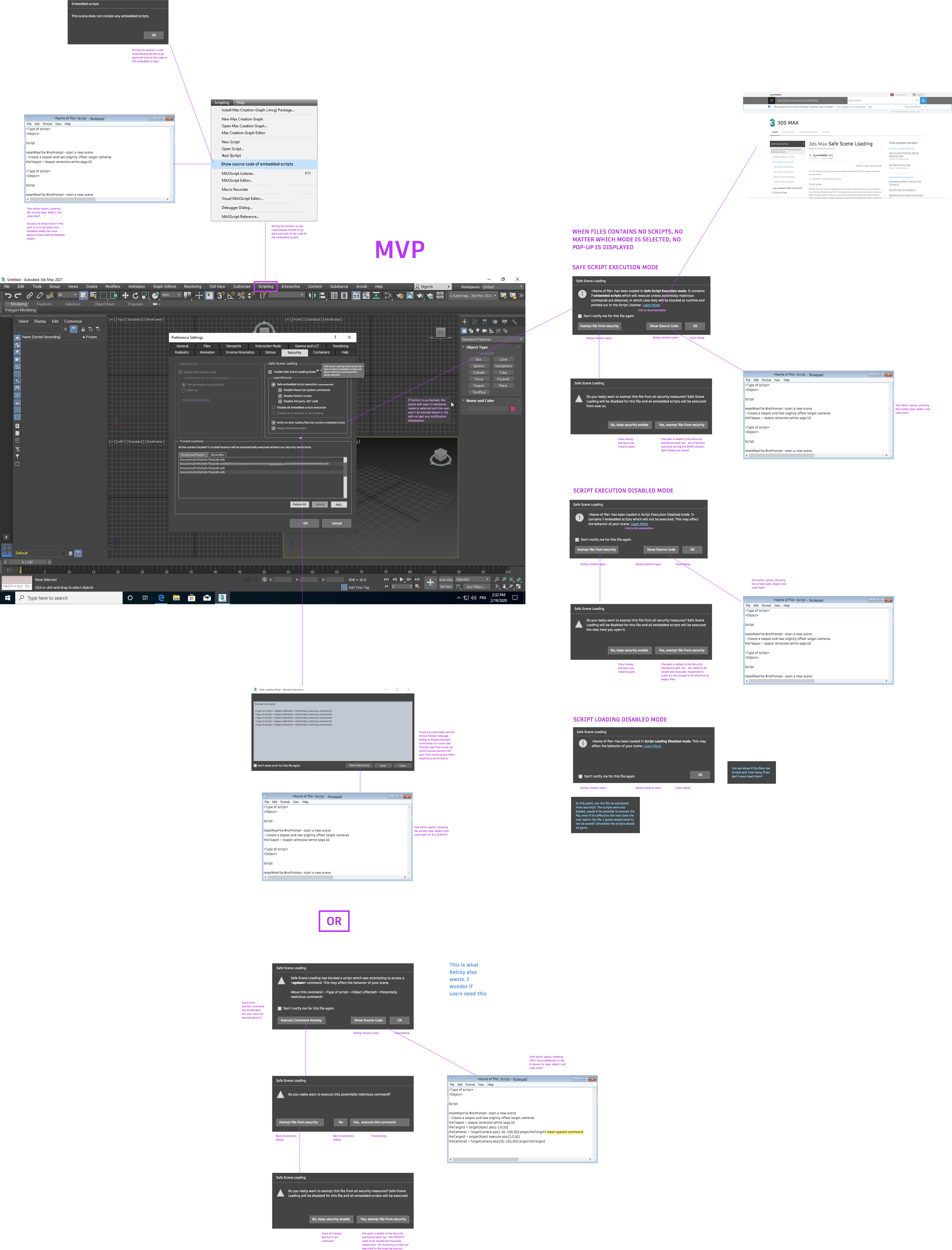
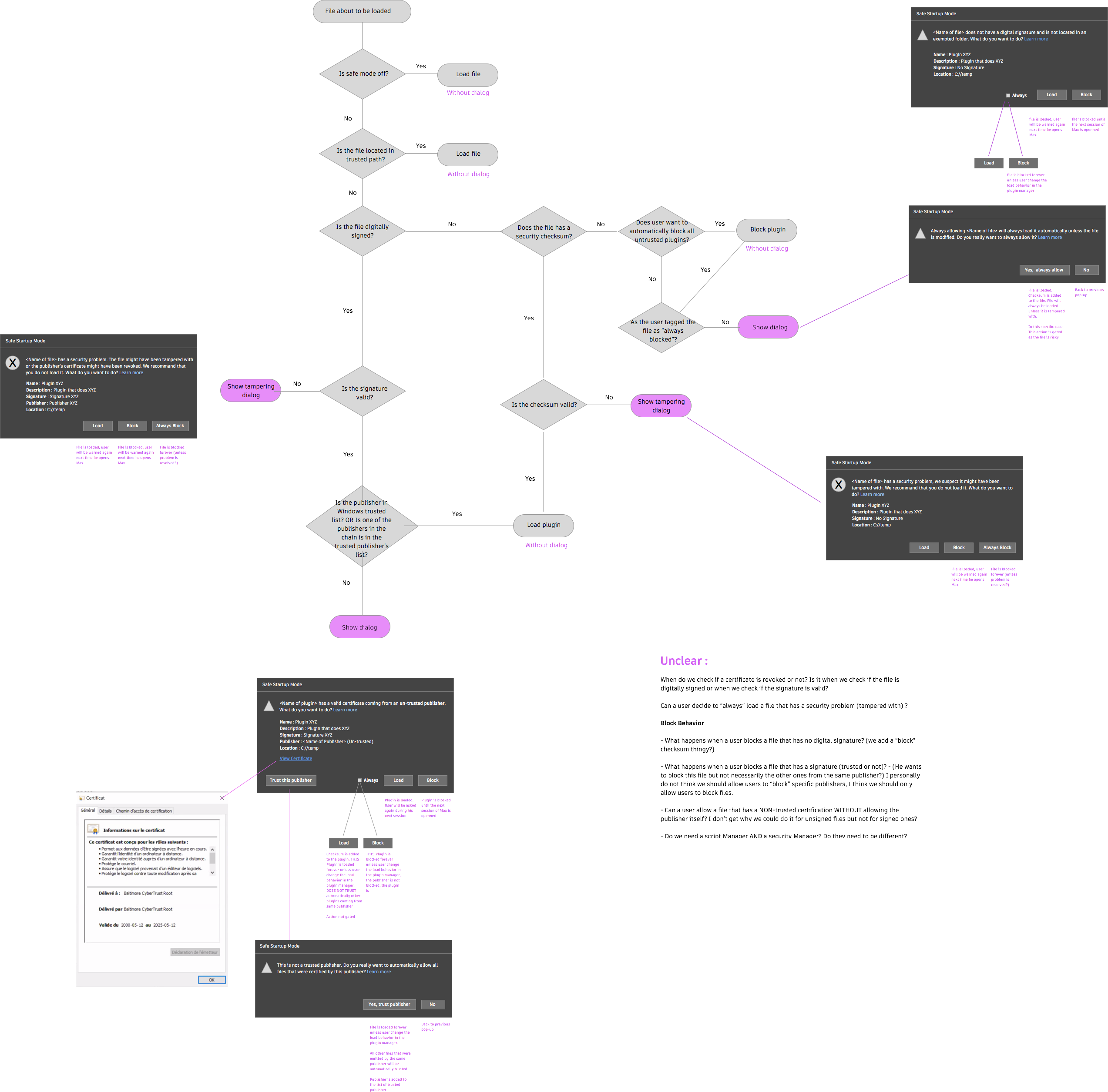
DIAGRAMS AND MOCKUPS FOR OTHER MITIGATION LAYERS

Security Award – TechX 2022
18 months after having been flagged by the Autodesk’s Infrastructure Security Team, 3ds Max received the award for best security across the company

``I have worked closely with Emilie for more than a year on software security related capabilities in 3ds Max. I really enjoyed working with Emilie because she is curious, dynamic (has a bias toward action) and always puts the user first. Software security is a pretty dry and convoluted subject, but Emilie jumped in with both feet and absorbed a huge amount of knowledge from me and our security tech-lead, so she can really understand the security tech-lead, the developers, and ultimately propose a workflow that minimizes the friction created by security restrictions and the user's normal workflows. Emilie delivered mockups with clear descriptions, kept track of countless variations and even designed a survey for our customers to help us learn if they care about security and how they use features that will be affected by security settings. I highly recommend Emilie``